The attack starts, innocently enough, with an email. But when someone clicks the link inside, hackers quickly take over.
Computers at the school, hospital, or city government are locked, and the only way for employees to get back in is to pay the attacker hundreds of thousands of dollars worth of Bitcoin.
Even then, there’s no guarantee they won’t do it again.
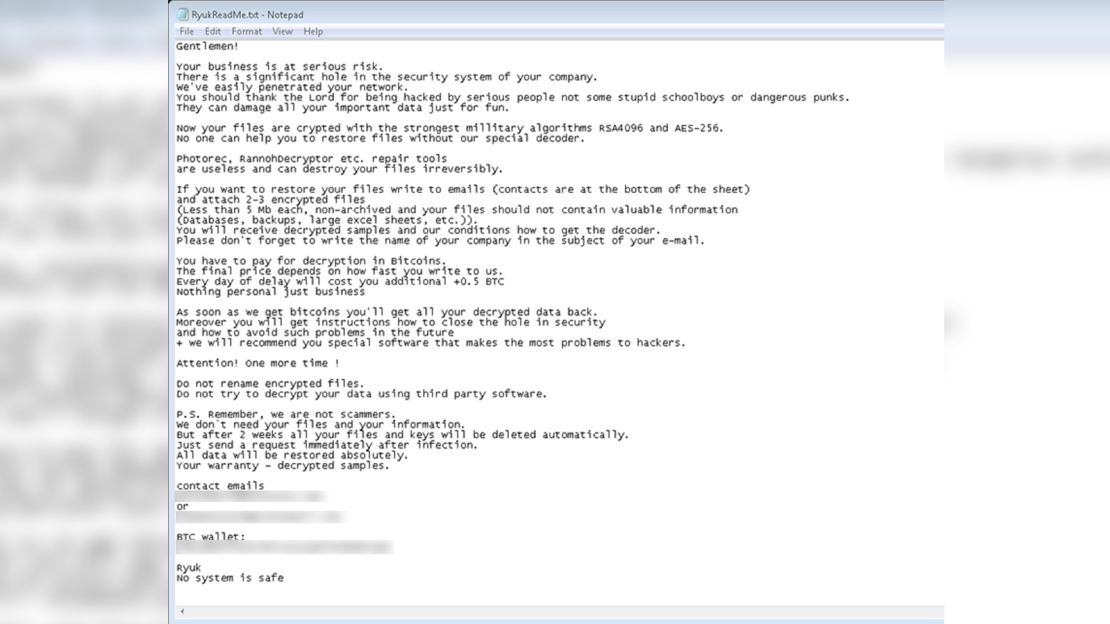
Welcome to the world of ransomware attacks, a rising form of malware that hackers use to infect a computer or network to encrypt files and data, crippling them to users, with a ransom dangled as the only way out.
Just this year alone, 140 attacks targeting public state and local governments and health care providers have been reported, according to a tally by the cybersecurity firm Recorded Future, which has tracked attacks on local governments since 2013 and the healthcare industry since 2016.
The attacks have targeted schools, local government offices and hospitals. One recent victim was a network of Alabama hospitals that had to stop accepting new patients because of a ransomware attack.
Last year, the firm tracked 85 attacks. That’s a rise of nearly 65%, an average of nearly three attacks each week.
Complicating officials’ abilities to track these attacks, many organizations choose not to report these incidents, hoping to avoid news coverage of the attack and resulting payout.
That means the total number is largely unknown.
“Undoubtedly the number of attacks this year across all sectors is in the thousands,” Recorded Future senior solutions architect Allan Liska tells CNN. “In fact, most security firms estimate that 2019 is set to see the highest number.”
How it works
The most common way for attackers to penetrate a network is through a phishing attempt. The attacker may send a seemingly innocent email to a colleague or you with a malicious link or an infected file attached.
Then, once the file is downloaded – the targeted person usually has no idea what they’ve done – the malware can infect your system and encrypt files on your computer, which locks users out and restricts access to them, and spread across your company’s network and infect other computers.
The hackers will then demand a ransom be paid out in order to have the files decrypted. Payment is typically requested in Bitcoin or some sort of virtual currency so they can remain anonymous before unlocking the files and data.
These attacks are serious – they can cripple entire infrastructures, sometimes preventing doctors from accessing critical patient charts or police departments from knowing what resources they have available for emergency calls.
And they’re only getting more prevalent – and harder to beat.
“Ransomware is a big problem that is continuing to grow,” said Liska. “It is also a big money making opportunity for both experienced and new cybercriminals. Which means the bad guys are devoting a lot of resources to developing new methods to deliver ransomware.”
The different styles and deployment methods used in ransomware is growing more sophisticated. Companies that use “weak and insecure” Remote Desktop Protocol (RDP) credentials, for instance – a way for businesses to connect one computer to another – are just one new way in, according to the FBI.
The latest victim is DCH Health System, a regional health care system located in West Alabama. Computers across its network of hospitals were infected last week after its network was penetrated, according to a statement released by DCH Health System.
While the hospitals in the DCH Health Systems network were still able to provide critical medical care to patients, it disrupted their ability to accept new patients.
“Our teams continue to work around the clock to restore normal hospital operations, as we incrementally bring system components back online across our medical centers.
“As we complete this process, all three hospitals will continue to be on diversion for all but most critical patients through the weekend. Our Emergency Departments will continue to see patients who bring themselves to the hospital,” DCH Health System said in a statement.
Officials for DCH Health System told Tuscaloosa News that the organization paid the hackers. DCH Health System said in a statement that a decryption key was obtained and that teams are working to restore its systems.
CNN has reached out to DCH Health System about the report that it paid the hackers but has not received a response.
“Healthcare is a particularly tricky area for ransomware,” Liska, the researcher who tracks the attacks, told CNN. “Many healthcare systems are locked down by vendors, so healthcare systems often can’t be patched in the same way other sectors can patch. This means that healthcare organizations have to take other measures to protect themselves.”
Much like real-life kidnapping cases, the FBI says victims shouldn’t pay the ransom. That only encourages continued criminal activity. Plus, there is no guarantee the files will be decrypted, and the affected files can become corrupted, rendering them unrecoverable.
“Systems infected with ransomware can also be infected with other types of malware that remain hidden on the system even if the victim decides to pay the ransom,” said a spokesman for the FBI. “Therefore, the FBI recommends that instead of paying a hacker’s ransom, victims perform a full remediation of any infected systems to include wiping their computers and restoring from offline backups.”
For many businesses, the cost of hiring specialists, replacing equipment and wiping out their computers is not a practical solution, as the costs can exceed the ransom payment by a wide margin.
Entire cities can be targeted
In another attack earlier this year, the city of Baltimore was targeted and the hackers demanded approximately $76,000. Mayor Bernard C. Young refused to give in, and the city has spent millions dealing with the fallout.
Baltimore councilman Isaac Schleifer shared information from a city budget meeting, and the early projected impact of the ransomware attack is estimated at $18.2 million. The city’s information technology office has spent close to $4.6 million on recovery efforts already, with an additional $5.4 million expected to be spent by the end of the year. The city anticipates the potential lost (or delayed) revenue to total $8.2 million.
The largest known payout in a ransomware attack this year was by the city of Riviera Beach in Florida, according to Liska. Officials approved a $600,000 payment in Bitcoins to a hacker that took over local government computers.
Punishing those responsible isn’t easy
From lone hackers to state-sponsored hacking groups, ransomware is becoming a more commonly used tool in cyber crimes and can be carried out from anywhere in the world.
A federal grand jury indicted Faramarz Shahi Savandi, 34, and Mohammad Mehdi Shah Mansouri, 27, of Iran last year for an international computer hacking and extortion scheme involving ransomware against the city of Atlanta.
The two men have been charged with conspiracy to commit fraud and related activity in connection with computers, conspiracy to commit wire fraud, intentional damage to a protected computer, and transmitting a demand in relation to damaging a protected computer.
And herein lies another problem: If the US is unable to locate and extradite the attackers, they may never be punished for their crimes.
The US Treasury Department further sanctioned North Korea in September after the US found evidence that the “Lazarus Group,” “Bluenoroff” and “Andariel” were “agencies, instrumentalities, or controlled entities of the Government of North Korea” responsible for “malicious cyber activity on critical infrastructure.”
The “Lazarus Group” is responsible for the massive WannaCry 2.0 ransomware attack in 2017, according to the FBI. The attack affected hundreds of thousands of computers across the globe, according to White House homeland security adviser Tom Bossert.
The main suspect in this case is Park Jin Hyok, who is allegedly a computer programmer that is part of the “Lazarus Group,” according to the FBI. While a federal arrest warrant has been issued for Park, he may never see the inside of a US jail for his crimes.
Everyone should be on alert
The FBI’s Internet Crime Complaint Center reported 1,493 victims with losses estimated at $3,621,857 in 2018. While the victim count has gone down from its peak in 2016 of 2,673 victims, the losses have only increased.
“The FBI becomes concerned anytime we see a rise in the number of victims and monetary losses associated with a threat,” said a spokesman for the FBI. “Clearly we have seen this trend with ransomware and we are working with our international partners, private industry, and other government agencies to bring the actors associated with ransomware to justice.”
While ransomware remains a financially motivated crime, Liska warned it can occasionally be done as a distraction attack carried out by cybercriminals or nation state attackers.
Attackers may be in a victim’s network for weeks, secretly stealing data and information. Then, in order to cover their tracks, they launch a ransomware attack to distract incident response teams as the attacker’s other activity may go unnoticed.
With eyes toward 2020, Liska said this type of attack is particularly of concern. “Voter registries and other election systems may be vulnerable to ransomware attacks and nation state actors have all added ransomware to their arsenal of tools,” he said.
CNN’s Tina Burnside, Kevin Collier, Pierre Meihan, Faith Karimi, Eli Watkins and Zachary Cohen contributed to this story.










