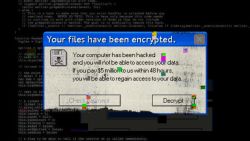
A devastating ransomware attack on a critical fuel pipeline in the United States has highlighted the growing threat that cyber criminals pose to the world’s largest corporations and strategic infrastructure.
It also raises a thorny question: should companies held to ransom yield to extortionists or resist making payments? Often it’s a choice between regaining access to IT systems for a fee so that operations can be restored, or running the risk of continued disruption that could have huge repercussions for employees, shareholders, customers, the economy and even national security.
In the case of Colonial Pipeline, which has yet to fully restore its operations, a lot is at stake. The pipeline delivers nearly half the diesel and gasoline consumed on the East Coast, and it provides jet fuel to major airports, many of which hold limited supplies on site. A growing number of gas stations are without fuel as anxious drivers rush to fill their tanks and American Airlines has been forced to add fuel stops on a couple of longer routes.

But paying the attackers risks encouraging even more ransomware assaults by demonstrating just how lucrative the business model can be. The FBI confirmed on Monday that the pipeline hackers are a criminal group originating in Russia named DarkSide.
One of the ways to discourage cybercrime and ransomware attacks is to “make it a less profitable endeavor,” according to Josephine Wolff, assistant professor of cybersecurity policy at The Fletcher School at Tufts University. “These groups will not continue to [launch attacks] if it’s not a viable business model,” she added.
DarkSide has already posted a notice on the dark web that their motivation was “only to make money,” according to Binary Defense, a cyber counterintelligence firm. The group offers “ransomware as a service,” said Wolff.
“They essentially sell ransomware attacks to customers,” she explained. “That’s a pretty strong signal that this is a profitable business.”
A thriving industry
The world has had plenty of warning. Four years ago, an unprecedented wave of ransomware attacks hit companies and organizations around the globe. In the United Kingdom, some hospitals were forced to cancel outpatient appointments and tell people to stay away from emergency departments.
And it will take a lot more than a handful of companies refusing extortion payments to deter cyber criminals.
“They’ll find another victim, another way of making money,” said Peter Yapp, the former deputy director of the UK National Cyber Security Centre and now a partner at Schillings.
“What will stop this is much higher levels of [cyber] security,” he told CNN Business. “Instead of putting money into paying people after the event, we should be putting money in ahead of the event and making sure we batten down the hatches,” he added.
Losses from cybercrime have surged in recent years. A report last year from the Center for Strategic and International Studies and software security firm McAfee put the worldwide cost of cybercrime at almost $1 trillion between 2018 and 2020.
“Cybercrime appears unstoppable … The risk of cybercrime to operations and profits continues to grow for many organizations,” it added.
That’s become a growing opportunity for insurance companies, with global cyber insurance premiums expected to increase from around $2.5 billion today to $7.5 billion by the end of the decade, according to PwC.
Cyber insurance policies typically cover ransom payments where they are legally permissible and if no sanctioned entities, such as terrorist organizations, are involved. But there are signs that this may be changing.
AXA (AXAHF) recently stopped offering ransom reimbursement as part of new cyber insurance policies in France in response to concerns raised by French cybersecurity officials.
In a statement, the insurer said that it is “waiting for the decision of the public authorities.”
“The subject of ransom reimbursement has become a key issue for cyber insurance … It is essential that the public authorities give concrete expression to their position on this subject in order to enable all market players to harmonize their practices,” the company added.
Speaking at a cybercrime conference in Germany on Monday, Thomas Sepp, chief claims officer at Allianz (ALIZF) Global Corporate & Specialty, said that the insurer advises its policyholders to work with authorities at an early stage and avoid paying ransoms if possible, “so as not to create further incentives for the commercial business model of hacker groups.”
“Of course, this has its limits when peoples’ lives and health are at risk,” he added.
How governments can help
While the US and UK governments provide advice and guidance to companies on how to handle cyberattacks, there is no official policy when it comes to ransomware payments.
For example, the FBI’s standing guidance is that victims should not pay a ransom in response to an attack in order to discourage perpetrators from targeting more victims. But multiple sources have previously told CNN that the FBI will, at times, privately tell targets that they understand if they feel the need to pay.
Asked on Monday whether Colonial had paid a ransom, senior White House officials demurred.
“That is a private sector decision, and the administration has not offered further advice at this time. Given the rise in ransomware, that is one area we’re looking at now to say what should be the government’s approach to ransomware actors and to ransoms overall,” said Anne Neuberger, the top official responsible for cybersecurity on the National Security Council.
According to Wolff of Tufts, governments need to provide greater clarity to businesses on what kind of resources and assistance is available to them if they don’t pay a ransom.
In extreme cases, companies could go under if they don’t pay a ransom and the wider impact on the economy could be huge. That’s why it’s not enough for law enforcement to simply say, “don’t pay … you’re fueling an industry,” added Yapp.
While it is not the job of governments to look after commercial entities, the growing wave of ransomware attacks suggests it may be time for law enforcement officials to step up efforts to go after cyber criminals, Yapp said.
“Commercially, it is having a huge drain on companies right across the world,” he added. The threat of “being found out and prosecuted” could in itself act as a strong deterrent, he said.
As critical national infrastructure networks become increasingly connected with other devices and systems over the internet, the danger posed by these attacks will only increase.
“Attacks targeting operational technology — the industrial control systems on the production line or plant floor — are becoming more frequent,” Algirde Pipikaite, cyber strategy lead at the World Economic Forum’s Centre for Cybersecurity, said in a statement.
“Unless cybersecurity measures are embedded in a technology’s development phase, we are likely to see more frequent attacks on industrial systems like oil and gas pipelines or water treatment plants,” she added.
— Zachary Cohen, Geneva Sands and Matt Egan contributed reporting.



![This photo taken on August 4, 2020 shows Prince, a member of the hacking group Red Hacker Alliance who refused to give his real name, using his computer at their office in Dongguan, China's southern Guangdong province. - From a small, dingy office tucked away in an industrial city in southern China, one of China's last "volunteer hacker" groups maintains a final outpost in its patriotic hacking war. (Photo by NICOLAS ASFOURI / AFP) / TO GO WITH China-hacking-security,FOCUS by Laurie Chen / The erroneous mention[s] appearing in the metadata of this photo by NICOLAS ASFOURI has been modified in AFP systems in the following, we removed the HOLD HOLD HOLD in the main caption. Please immediately remove the erroneous mention[s] from all your online services and delete it (them) from your servers. If you have been authorized by AFP to distribute it (them) to third parties, please ensure that the same actions are carried out by them. Failure to promptly comply with these instructions will entail liability on your part for any continued or post notification usage. Therefore we thank you very much for all your attention and prompt action. We are sorry for the inconvenience this notification may cause and remain at your disposal for any further information you may require. (Photo by NICOLAS ASFOURI/AFP via Getty Images)](https://media.cnn.com/api/v1/images/stellar/prod/210621154549-hackers-keyboard.jpg?q=x_0,y_131,h_1419,w_2523,c_crop/w_250)