Story highlights
There have been more than a dozen attempts to attack the Healthcare.gov web site
None of the attacks have been successful, officials said
Officials also hired an "ethical hacker" to try to find holes in the system
HealthCare.gov went live on October 1; beset by internal problems since
Hackers have attempted more than a dozen cyber attacks against the Obamacare website, according to a top Homeland Security Department official.
The attacks, which are under investigation, failed, said the official.
Authorities also are investigating a separate report of a tool designed to put heavy strain on HealthCare.gov through a so-called distributed denial of service. It does not appear to have been activated.
“We received about 16 reports from HHS that are under investigation and one open source report about a denial of service,” according to Acting Assistant Homeland Security Secretary Roberta Stempfley of the Office of Cybersecurity and Communications.
Related: Many in Congress avoiding health care exchanges
Stempfley testified at a hearing of the House Homeland Security Committee that the attempts were made between November 6 and November 8, but none were successful.
The DDOS program, called “Destroy Obama Care,” was recently spotted on a “torrent” file sharing web page, and first reported last week on a blog by Arbor Networks, which said it found no evidence the program had actually been launched to attack the troubled federal portal for consumers to shop for health coverage.
“We have not monitored any attacks. We have not seen any sizable, or anything to believe that these problems are related to DDOS,” said Dan Holden director of security research for Arbor Networks, adding “I don’t believe that the problems with the site’s availability is due to any kind of DDOS attack.”
Related: White House officials get earful from Democrats on Obamacare
In a separate hearing, a top Health and Human Services official, Chief Information Officer Frank Baitman, said his department had engaged an “ethical hacker” on staff to test the defenses of the health care site.
The hacker discovered between seven and 10 items related to attempted security breaches which were disclosed in a report.
Baitman said he would not describe these items as serious and said the majority had been resolved.
The use of hackers employed to test on line site security is common, Holden said.
“That’s pretty standard practice, generally referred to as penetration testing,” Holden told CNN. “There are many companies and individuals out there that have done that for a very long time. The idea being, you want to know where your weaknesses are and what the potential of attacks could be.”
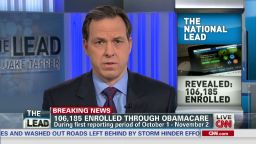
Related: Obamacare’s first month: 106,000 signed up
But others are still concerned about the security of the site.
In statements made before the House Homeland Security hearing, database expert Luke Chung –whose company did not work on HealthCare.gov – provided his technical assessment, saying that the problem with the roll out of the website was far deeper than “too many users.”
Chung said that in his estimation the skill set of the designers of the website were subpar, adding that “when you have an environment where the developer can barely get the web site functional, security is way down on the list of things to take care of. Security has to be built-in at the very beginning not at the very end.”
But, critical infrastructure protection specialist and CEO of Lunarline, Inc., Waylon Krush told the committee, “There’s not a system out there that’s perfect in nature, by any means, from a cybersecurity perspective.”
“You would assume that for hundreds of millions of dollars it would be a secure site,” said Chung.